Risk & Threat Preparedness: The Fundamental Guide
Australian Standard (AS) 3745:2010 Planning for Emergencies in Facilities, is a standard which has undergone a lot of evolution over its near 30 years of existence. It started off as an outline for procedures involving Emergency Control Organisations (ECO), buildings, structures, and workplaces – however over time and with various additions it began incorporating a broader view to include various emergencies and personal emergency evacuation plans.
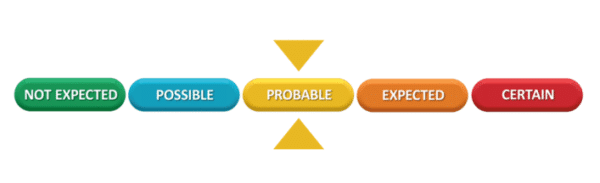
In 2015, the Australian Government changed the National Terrorist Threat Advisory system from a four-tiered system to the five-tiered system now in place. Currently, the National Terrorist Threat Advisory level is at ‘PROBABLE’. Credible intelligence as assessed by Australia’s security and intelligence agencies indicates there are individuals or groups within Australia that have both the intent and the capability to conduct a terrorist attack within our shores. However, not all threats are related to terror but domestic concerns.
In this master guide, we break down the principles & methodologies of risk & threat preparedness as covered in the Australia-New Zealand Counter-Terrorism Committee (ANZCTC) guide to protecting crowded places, to provide you with an understanding of the newly evolving yet crucial landscape.
Table of Contents
1. What is Risk & Threat Preparedness?
2. Recent Incidents in Risk & Threat
3. Different Types of Risks & Threats
4. Responding to Threat Scenarios
What is Risk & Threat Preparedness?
The threat and security environment continues to evolve and has been rapidly changing in the past decade within Australia. In September 2014, the Australian Government showed they had begun to take these new threats seriously as they raised the National Terrorist Threat Advisory Level from medium to high.
In November 2015, this system was once again revised to incorporate a new five-tier classification system, which is now currently sitting at ‘Probable’ as seen below:
This new rating indicates the Australian government, intelligence, and law enforcement agencies have identified elements exist within our borders that have both the intent and capability to conduct a terrorist attack in Australia.
On 20 August, 2017, Australia’s former prime minister Malcolm Turnbull released the first reference guideline for risk & threat preparedness – Australia’s Strategy for Protecting Crowded Places from Terrorism. This initial document was the first spark which led to countless other documents being drafted, which are still used by the ANZCTC as well as the Australian Security Intelligence Organisation (ASIO) and other subject matter groups.
Whether politically motivated or not, risk overall has escalated due to increased criminal activity, domestic violence, mental illness, and active threats (terrorist-related or otherwise). These threats simply cannot be ignored in a facility’s Emergency Management Plan – as such, First 5 Minutes Risk & Threat Preparedness service offering prepares clients from these evolving and less obvious risks and threats through audits, risk assessments, training, and consultations.
Incidents in Risk & Threat:
When it comes to risk & threat related incidents, it is important to always remember they can happen at anytime and anywhere. Even in areas or ways which are least expected, if there is even the slightest chance for it to occur you must be prepared.
In the last 3-7 years, states all over Australia have experienced tragic active threat incidents including:
- Victoria: 2018 Bourke Street incident

Source: https://en.wikipedia.org/wiki/2018_Melbourne_stabbing_attack
On 9 November 2018, one male attacker set his vehicle on fire and stabbed three innocent people on Bourke Street in Melbourne. After the acts of terror were committed, the attacker was fatally shot by Victorian Police. Of the three victims that were stabbed, one died at the scene whilst the others were sent to hospital for treatment.
The details of the attack were as follows:
- At 4:20pm, the attacker set fire to their Holden Rodeo Ute on Bourke Street in Melbourne.
- They emerged from the vehicle before it burst into flames, drawing attention to himself from pedestrians.
- He used a knife and went on a stabbing spree wounding innocent people. Once police arrived, the threat was neutralized, and the incident was thankfully resolved.
The next day the Premier confirmed “what we saw yesterday was an act of terror.” A counter-terrorism investigation was launched to ensure there were no accomplices and no planned follow up attack.
- New South Wales: 2014 Lindt Café siege

Source: https://en.wikipedia.org/wiki/Lindt_Cafe_siege
The attack lasted from the 15 to 16 December 2014, was an act of terror by a lone gunman who held ten customers and eight employees hostage in the APA building Lindt Café in Sydney City Centre. The siege led to a 16-hour standoff between police officers and the gunman the details which were as follows:
- At 8:33am the gunman entered the Lindt Café, an hour later forced the café manager to phone 000.
- After pulling out his weapon, the gunman used hostages as leverage and human shields from police and disabled the automatic sliding glass doors of the café.
- The gunman then made claims to police and media broadcasts (through hostages) that there were four explosive devices located throughout Sydney which would be detonated if his demands were not met. These devices were never found during investigations post-attack.
- Immediately a staged exclusion zone was established, buildings were evacuated around and above the café, residents of other buildings were advised to stay indoors away from windows, and a suspicious package was removed from a nearby building by police.
- A demand was made to speak with the Australian Prime Minister, which was declined. No further negotiations between police and the gunman took place according to hostages when interviewed post-attack.
- As the stand-off continued a total of five hostages were able to escape through varying exit points including the front door, fire escape and another side entrance. After these escapes were noticed the gunman threatened to take the lives of the remaining hostages.
- It was not until the next day when more hostages attempted an escape that a loud gunshot was heard from inside the café.
- Upon hearing the shot, the Tactical Operations Unit stormed the café to ensure the safety of the hostages after cooperation from the gunman was evidently not possible.
- South Australia: 2017 South Australia Riverland school massacre plot

Source: https://www.abc.net.au/news/2019-03-01/teens-plead-guilty-over-alleged-riverland-massacre-plot/10862246
In November 2017, two teenagers had planned and were poised to take the lives of fellow high-school students in the Riverland Region of South Australia through an intended massacre using bombs and knives.
Fortunately, their plot was discovered merely days before they could strike.
Police uncovered a stash of homemade bombs, knives and body armour. It was believed that the attack was planned to happen less than 7 days from discovering the weapons, which would have been catastrophic.
Despite being found before it occurred, there truly was a real threat present in this situation. It was actively planned and highly likely to be carried out had there been no interference from the police. Knowing how to respond to even planned threats is extremely important to mitigating risk and ensuring well-being.
- New South Wales: 2015 Parramatta shooting

Source: https://en.wikipedia.org/wiki/2015_Parramatta_shooting
In October 2015, a 15-year-old boy shot an unarmed police officer outside the NSW Police Force Headquarters in Parramatta, Sydney. In the days leading up to the shooting, police reported they were aware of an increase in ‘chatter’ related to a potential attack occurring.
Police investigated the crime as an act of terror. Investigations into the motivations for the attack were made, but it was suspected the attack was influenced by ideological factors.
Police responded by arresting the perpetrator, alongside the firearm supplier and other students at the perpetrators high school who allegedly posted threatening material on social media.
In response to the situation, a new legal change was approved by the Australian Attorney-General allowing control orders to be made on people aged 14 and over.
- New South Wales: 2017 Queanbeyan stabbing attacks

Source: https://www.abc.net.au/news/2017-04-07/counter-terrorism-police-join-investigation-into-fatal-stabbing/8425580
In April 2017, two boys attacked a service station attendant at Queanbeyan with a knife. This incident was simply the beginning of a crime spree which continued for the next 14 hours. Further attacks were made in a local park, a victim’s home and an individual’s car who was flagged down by the attackers.
The pair of attackers were eventually arrested after a car chase on Montaro Highway; they were ordered to appear at Children’s Court where they were both sentenced to jail time.
The attack led to dramatic increases in security precautions in Australia, including the installation of hundreds of security bollards across the entire nation. Additionally, discussions have begun to introduce maximum security prisons for 16-year-old offenders, to deter similar incidents happening in the future.
- Melbourne: 2017 Brighton siege

Source: https://www.abc.net.au/news/2021-03-15/brighton-siege-yacqub-khayre-coronial-inquest/13247902
In June 2017, a female escort was booked through an agency to meet in an apartment at the Buckingham International Serviced Apartments. Once the escort arrived at the agreed apartment, they were taken hostage and held captive. A call was made to local police by the offender that they were holding a hostage.
Specialist police forces were called in to respond to the terror incident; both the Critical Incident Response Team (CIRT) & Special Operations Group (SOG). After a few hours had passed, the perpetrator exited the apartment building yelling, running, and attacking the responding officers. The perpetrator was taken down by police, and the hostage was freed without any physical harm.
During the investigation, the siege incident became labelled as a terrorist incident. It led the Prime Minister at the time to recognise, “a growing threat from … terrorism” and caused a change to parole laws in Australia. The attack also led to the first national amnesty since 1996; a firearms amnesty to hand in unregistered or unwanted firearms to reduce the deteriorating security environment.
- New South Wales: 2017 Australian airplane bomb plot

Source: https://ctc.usma.edu/operation-silves-inside-the-2017-islamic-state-sydney-plane-plot/
In July 2017, what has been described as one of the most ambitious terror plots that Australia has faced was stopped after the arrests of four suspects. The plan involved bombing an international flight out of the country whilst also creating a chemical weapon to disperse lethal gas against members of the public.
What had set this plot apart from those before it was not only it is vast intricacy, but also how close the plot came to fruition before it was stopped. It had progressed undetected for over six months before Australian authorities became aware as a result of international intelligence being passed forward.
In addition, although terrorism plots guided by remotely given instructions were not new, this was the first time that materials to use in the plot were also distributed remotely. It caused security agencies across the globe to take note of new innovations from attackers, to determine new measures to ensure new risk & threat security countermeasures would be implemented.
Different Types of Risks & Threats We Face
The landscape continues to expand, so do the types of risks and threats which a facility must prepare themselves. Below we run through examples of risks & threats to prepare against:
1. Armed Offenders in Crowded Places
Crowded places have been specifically identified – nationally and internationally – as particularly attractive targets for those planning to engage in acts of terrorism, or those who are disgruntled with mental impairments. Active armed offender attacks are the most common acts of terror and will continue to occur in crowded places such as sporting stadiums, transport hubs and entertainment venues.
The large numbers of potential victims are what make these settings highly likely to experience acts of terror. The attendants have a reduced situational awareness due to the nature of the event/setting, thus making it easier for armed offenders to commit their violence.
In Australia, despite weapons such as knives and firearms being regulated, the use of these weapons in an armed offence is considered reasonably feasible. Several attacks targeting places such as shopping centres, universities and public spaces have occurred or been disrupted. These attacks present a real threat to the community.
Below are key features of an active armed offence:
- Incidents often occur in crowded places where the offender has access to many potential victims.
- Incidents evolve rapidly and reach resolution quickly.
- Offenders will continue to attempt to harm victims until law enforcement arrives.
- These incidents are most likely not resolved through negotiation or peaceful means.
In most cases, incident responders or emergency responders require freedom of movement and ready access to victims to achieve their objectives of resolving the incident whilst keeping victims safe. Therefore, minimising the offenders access to potential victims should be the primary objective of any plans or strategies, which is achieved through:
- Initiating immediate response arrangements.
- Restricting offender movements.
- Minimising the duration of the incident.
- Move people away from the danger zone.
- Preventing people from entering the scene.
- Helping police locate and isolate the active armed offender.
Consider the following equation:
TIME + FREEDOM OF MOVEMENT = INCREASED CASUALITIES
To reduce the casualties of an incident, it is most effective to reduce the timeframe of the incident and reduce offenders movement.
Responding to and mitigating these incidents consists of four distinct parts Prevention, Preparedness, Response and Recovery. These steps are all contained in Australia’s National Counter-Terrorism Plan:
Prevention:
Despite the importance of complete prevention, it is not often possible to stop armed offences before the event occurs. Prevention should therefore have a broad meaning to encompass activities that may reduce the severity or impact of the emergency event.
There are several prevention activities that can be used including: gathering & analysing intelligence, developing strategies to reduce the impact on life, and identifying or eliminating vulnerabilities at potential target sites. Overall these prevention techniques must aim to:
- Audit & assess the threat and risk to address vulnerabilities.
- Deter a would-be attacker through obvious physical and electronic security measures.
- Detect any intrusion.
- Develop a proactive protective security posture.
- Delay or limit the intrusion for a sufficient period to allow a response force to attend.
- Mitigate or reduce the severity of the incident.
- Restricting the movement of the offender whilst reducing access to victims.
Not all crowded places will share the same risk profile or have similar vulnerabilities, so facilities must adapt their prevention-related activities to suit their space.
Preparedness:
Activities which relate to preparedness include risk assessment, emergency planning, resourcing, capability development and testing of preparedness arrangements. Due to the unexpected and dynamic nature of armed offender events, crowded place owners and operators should consider adopting a ‘contingency planning’ approach to these incidents.
Contingency threat preparedness enables a situational approach to responding to emerging threats in unexpected situations. These plans supplement the general emergency response plans which facilities require for other emergency types.
Some of the basic features of these contingency plans include:
- Combined and coordinated management, using a multi-stakeholder approach.
- Assessment of the crowded place and the potential consequences of an attack at that location.
- The application of emergency response arrangements must be flexible, scalable, and appropriately applied according to the nature and impact of the crisis.
Response:
The response can be broken down into two distinct phases: initial response & police response.
As part of the initial response victims of the attack are advised to follow this three-step sequence.
- Escape: The priority during is to remove victims from close proximity of the offender. If it is safe, any occupants of the crowded area or facility must evacuate and escape the situation as soon as possible.
- Hide: If it is unsafe to evacuate or occupants are unable, they must shelter/hide and take advantage of any available concealment or cover from offenders. As the situation progresses, occupants should consistently re-evaluate their escape options as they hide.
- Tell: If it is safe, information should be provided immediately to the police force via 000. This should never be done at the expense of anyones safety.
Police in each state and territory have robust systems and inter-agency arrangements to achieve the following objectives:
- Saving lives and minimising the risk of severe injury of victims – achieved through rapid deployment strategies.
- Locating and isolating the offender of the attack to reduce access to victims.
- Resolving the situation by moving toward the threat in a sustained pace to defeat or disarm the offender.
- Establishing a common and control arrangement once first responders have already arrived at the scene, to ensure a more controlled response.
Recovery:
The final stage of mitigating incidents is the smooth transition from response to recovery, where the following should occur:
- Public information released and community confidence restored.
- Scene preservation and investigation activities.
- Business continuity practices put in place to restore business activity.
2. Chemical Weapons in Crowded Places
A chemical weapon is a device or mechanism designed to deliberately deploy a harmful chemical, using the toxic (rather than explosive) properties of the chemical to produce physiological effects on victims.
These chemicals and thus chemical weapons vary in toxicity, with some being highly toxic with immediate or delayed symptoms whilst others are less harmful and pose less of a threat.
The toxicity and chemical concentration when it reaches the intended victims will determine the severity of the exposure. The concentration of a chemical is determined by:
- The volatility, state, vapour density and persistence of the chemical.
- Environmental factors and their strengths – e.g. wind, rain, humidity.
- Where the chemical is released – is the space enclosed, ventilated, multi-story?
What are the indicators of a chemical weapon attack?
One of the most difficult things about identifying chemical attacks is the variety in how different chemicals act and their differing indicators. In some cases, there may be next to zero immediate or obvious indicators of a chemical weapons attack.
Key considerations for a suspected chemical attack include:
- Eye irritation, changes to vision, vomiting or diarrhea.
- Coughing, breathing or respiratory irregularities.
- Sudden muscle weakness, paralysis, or seizures.
- Skin redness, irritation, and burns.
- A collapse, loss of consciousness or death.
Other key signs outside the response of people include:
- Leakage of gas or vapour.
- Chemical reactions from an item or substance.
- Any powders, liquid, or other such substance releasing from an item/place with no logical explanation.
What can owners and operators do to protect crowded places & facilities from chemical weapon attacks?
There are a range of measures that owners and operators can employ to strengthen their ability to detect, deter, delay, and respond to terrorist attacks that have used chemical weapons. These measures include:
- Conduct a comprehensive review of current emergency and evacuation plans ensuring they are relevant and up to date with the current national threat level of probable.
- Ensure all occupants are aware of their roles during emergency situations, including the Emergency Control Organisation (ECO).
- Pre-plan evacuation routes, identifying alternative routes for escape to minimise occupant exposure to contaminated areas.
- Communicate evacuation routes effectively to occupants before & during incidents.
- Ensure all staff are briefed on the possible health effects of a chemical weapons attack.
- Ensure occupants are aware of the mechanisms for reporting suspicious articles & individuals, including to call 000, local police or Crime Stoppers.
- Develop and conduct robust mail screening procedures to ensure harmful weapons are not delivered to the facility.
- Conduct regular evacuation exercises to ensure they are suitable for maximising occupants’ safety.
- Ensure compliance with security plans and white level inspections through appropriate management and supervision.
A chemical weapon attack with roots in Australia:
In the 1990’s one of Australia’s largest sheep stations situated on the Eastern side of Western Australia, Banjawarn Station, was purchased by the Japanese doomsday cult Aum Shinrikyo.
The Japanese cult was responsible for many criminal and terrorist acts during that period. The purchase of the station was made when one of the cults deputy leaders visited the station citing that they were interested in uranium mining in the area.
Once the station was purchased, witnesses reported seeing individuals arriving at the station wearing full-length suits and helmets. It was later reported that these individuals arrived at the station with hydrochloric acid mislabelled as soap, and it was being tested as weaponry for the cults acts of terror.
Additional chemicals discovered by Australian Officers included ammonium chloride, sodium sulphate, perchloric acid and ammonium water. Once all materials were discovered they were seized by Australian authorities.
Mere months after the site was purchased, the cult group released toxic sarin gas into part of the Tokyo subway system resulting in thousands of causalities to the public. This incident was later linked to the purchase of Banjawarn station and the testing that had occurred there.
Despite no chemical weapon attacks ever occurring in Australia, incidents like these show just how important it is to remain vigilant to the possibility of not only chemical attacks but also related activities occurring within Australian shores.
HOT UP Principle:
To determine if the item is worthy of suspicion, it is best to apply the ‘HOT UP’ principle:
- Obviously suspicious.
- Typically, not in the environment in which it is found.
- Unauthorised access to the facility was made.
- Perimeter breach was made.
If an item is deemed suspicious, owners and operators should:
- Avoid touching, moving, or disturbing the item.
- Try to locate the owner of the item by inquiring with occupants in the vicinity.
- Check CCTV footage is available to discover how the item was placed and the owner of the item.
- Inform facility supervisors, management, or police if the item is not accounted for by anyone.
- Take a photo of the article to use when reporting it to the authorities.
- Take precautions to ensure occupants stay away from the item until authorities arrive.
Finally, chemical weapon attacks may cause panic & chaos in crowded places that is difficult for owners and operators to control. Thus, the following actions should be taken to protect lives during a chemical weapons attack:
- Contact and provide relevant information to emergency services.
- Activate existing emergency management plans, including evacuation procedures.
- Contain the incident or threat where possible.
- Assess the incident to best build situation awareness for where certain procedures in emergency plans or evacuation responses should not be taken.
What can the public do?
There have been numerous events where a member of the public has had a suspicion of ‘something not being quite right’ and reporting it to police. In these scenarios where a threat was present, many lives have been saved from harm.
Members of the public, general occupants and first-time facility visitors are often best placed to detect suspicious behaviour or unusual items in a facility. These suspicions should always be reported to 000 if owners and operators are not within a reasonable distance.
If a volatile chemical that would cause harm is released, individuals should:
- Minimise their chances of exposure by moving away from the release and avoiding any contact with their skin.
- Find uncontaminated air as quickly as possible – exit enclosed spaces or break windows to access clean air.
- Follow emergency responder instructions when they arrive on the scene.
- Once away from the chemical:
- Remove clothing and place them into a sealed plastic bag.
- Wash with soap and water rigorously, flush eyes with water if they are irritated.
- Seek medical attention if exposed to any chemical at all, even if there are no symptoms present.
- Avoid any plumes or vapor clouds.
- Consider wind direction and move away from the wind.
- Move uphill or upwind, if possible, away from the chemical release.
- If the situation calls for it, seal the building so that the chemical is contained within an enclosed space.
3. Hostile Vehicles in Crowded Places
Hostile vehicles present a constant threat to public spaces and the safety of occupants of facilities. They are classified as a vehicle whose driver is determined to access a restricted or unauthorised area or location by force, to cause injury or death to people, disrupt business or effect publicity for a cause. Hostile vehicles are outfitted with some form of explosives and travelling at a high speed which presents the primary danger to individuals.
The methods of hostile vehicle attack can take many forms including:
- Parked vehicle containing harmful materials or explosives.
- Encroachment
- Exploiting gaps in site defences.
- Tailgating through an active barrier system.
- Tampering with vehicle barriers to later provide unlawful vehicle access to an area.
- Penetrative impact to people or structures.
- Entry using deception.
- Duress against a security guard or employee to open a security gate.
How do we separate hostile vehicles from pedestrians in outdoor settings?
The best way to protect innocent people from hostile vehicle attacks is through the design of the public space. It is important that not only is the space made safe but also functional, such that the level of security is proportionate to the level of risk.
A ‘one size fits all’ approach to pedestrian safety does not apply to this type of threat. Not only do spaces require different solutions to ensuring safety, but methods of hostile vehicle attacks evolve, meaning new security measures must consistently be considered to reduce these risks.
The considerations that must be made when designing a space for safety and functionality include:
- Business needs.
- Logistics of the space – traffic management and operational requirements.
- The amount of pedestrian and vehicle traffic in the space.
- Any disability legislation which exists.
The above are identified through risk management plans (including vulnerability assessments) to understand the impact of certain design changes to the space in terms of safety and function.
To design spaces in a safe manner, a strategic implementation of steps, columns and structures offer a holistic approach of how vehicle mitigation can be applied in a subtle yet functional way. This method of design is best known as Crime Prevention for Environment Design (CPTED).
For example, a flight of steps which lead into the entranceway of a building will provide natural protection from hostile vehicles in the form of restricting access. Other forms of mitigative devices can include:
- Spheres
- Planter boxes
- Seats
- Bollards
- Structural/sculptural installations
- Bollards – either automatically or manually removable
- Water features
- Trees
- Columns
- Fences
- Mechanical/active barriers
- Gates
- Rivers
- Lakes
- Densely wooded areas
- Steep slopes
Here is an example of a before and after, for designing a space for hostile vehicle attacks:
Before:
After:
All barriers and hinderances help to create clearly defined pathways for pedestrians and vehicles which are separate from one another. To ensure that an even distinction is made between pedestrian and vehicle pathways, designers can use:
- Raised footpaths
- Cobbles near gutters
- Lights on the ground for cars to not exit – especially useful in car parks
- Medium strips
Not all deterrents are appropriate for each space and considerations must be taken in the design of the space to make sure the best deterrents are used. For example, a space which does not have raised gutters between the roadway and pedestrian pavement would not use a seating bench as a mitigation device as pedestrians would have a higher likelihood of injury in the event of vehicle impact.
4. Improvised Explosive Devices
Explosives remain a favoured terrorist weapon globally, due to their proven ability to inflict mass casualties, destroy property, cause fear, and attract media attention.
Improvised Explosive Devices (IED’s) are low cost, simple to construct and comprise of materials that are readily available and can be acquired without attracting undue attention.
IED terrorist attacks continue to be a threat to Australia, as demonstrated by recent counter-terrorism arrests and prosecutions of Australian-based violent extremists. For example, in December 2016 a Melbourne teenager was sentenced for his role in a disrupted IED plot in May 2015, where it was uncovered that the arrested individual as well as seven others wanted to detonate the devices around Federation Square on Christmas Day.
In what was described as ‘the most substantial terrorist plot that [has] been disrupted over the last several years’ police were able to stop the multi-modal attack, however this incident proved that IED attacks remain a risk & threat to crowded places.
What is the proper plan for responding to IED attacks?
Responding to and mitigating these incidents consist of four distinct parts – Prevention, Preparedness, Response and Recovery. These steps are all contained in Australia’s National Counter-Terrorism Plan:
Prevention
Not all risks or emergencies can be prevented. Therefore, in the case of IED attacks prevention should have a broad meaning to encompass all activities that may reduce the severity or impact of the emergency event.
Key ways to reduce harm or impact include:
- Limiting damage to structures and people – an explosive attack against a building can protect casualties due to harmful debris.
- Defining and maintaining stand-off distances – every metre of stand-off distance counts a significant amount toward ensuring occupant safety.
- Preventing progressive collapse – buildings undergo progressive collapse when a primary structure falls. Buildings should be designed with this in mind.
- Using the built and natural environment – by restricting public movement (also known as ‘compartmentalisation’ measures), IED attacks can have mitigated effects.
Preparedness
By incorporating emergency planning, resourcing, capability development and testing of preparedness arrangements, facilities can be better prepared for IED attacks. Key activities of preparedness include:
- Identifying and assessing suspicious objects or activity – this is not an exact science, but a matter of context.
- Use the HOT UP principle to assess an unattended or suspicious item, and combine it with other broader considerations
- Hidden
- Obviously suspicious
- Not typical
- Unauthorised access
- Perimeter breach has occurred
- Make sure to look out for nervous behaviour signs or behavioural clues that give an indication of preparing for terrorism.
- Continuous scanning of the area.
- Clock watching.
- Avoiding security personnel.
- Unusual video recording.
- Taking measurements and drawing diagrams.
- Asking about security operations.
- Weak cover story when questioned on their activities.
- Use the HOT UP principle to assess an unattended or suspicious item, and combine it with other broader considerations
- Inspection procedures for threats – if a potential threat is communicated, it can be necessary to conduct either a general cursory or white level inspection.
- General cursory inspections are brief inspections which do not pay much attention to detail; have authorities give the situation a second look.
- White level inspections are a detailed investigation of an area for anything suspicious, unusual or things that cannot be accounted for. These searches do not involve specialist investigators.
- If the threat is credible, it is best to seek the assistance of investigative specialists and police.
- Regularly reviewing and testing policies and procedures.
Response
The explosion or potential for explosion from an IED is likely to create a level of panic that is extremely difficult to control. The main objectives for a facilities response plan should include:
- Save/protect life.
- Facilitate evacuating at risk individuals.
- Contain the incident.
- Support emergency response and investigating activities.
- Tell occupants and visitors what they should do.
- Provide information to the relevant authorities.
When is evacuation the appropriate response to an IED threat?
If a threat has been received through a communicative transmission, one of the tougher challenges for management is deciding whether to evacuate. The decision should be based on an assessment of the credibility of the threat.
Once an evacuation has been decided to be carried out, there are two types of evacuations which can occur:
- Total evacuation: where all occupants leave the premises/facility.
- Partial evacuation: if the suspicious item is small enough or confined to one space, only a portion of occupants evacuation the premises/facility. Partial evacuations reduce the risk of injury to occupants, whilst also allowing critical services to continue for the facility.
Recovery
The final stage of mitigating incidents is the smooth transition from response to recovery, where the following should occur:
- Public information released and community confidence restored.
- Scene preservation and investigation activities.
- Business continuity practices put in place to restore business activity.
Escape, Hide, Tell – Responding to threat scenarios:
In the event of an immediate active threat scenario occupants must be prepared to take the actions necessary to reduce the likelihood of harm to themselves. During these high-pressure scenarios, it is understandable that their fight or flight response may cause them to take actions they would not normally take.
To make sure occupants come out of the situation as safe as possible, it is important that they follow the Escape, Hide, Tell protocol when in an immediate threat environment.
Escape
During an emergency, an individual’s priority is get as far away from the incident as soon as possible, if it is safe. Always ensure that the quickest and safest route is taken from the facility or incident.
If it is unsafe to run away or escape from the situation, then take cover as soon as possible.
When escaping, an individual may be frantically trying to bring some of their belongings with them that are sentimental, or they believe they will help them escape safely. The most important item that a person should prioritise taking with them is their mobile phone. All other items can be left behind if they hinder escape efforts.
Occupants are trained for fire emergencies, the protocol for evacuations is to always wait at the designated assembly areas which are determined the best spots to congregate after the emergency. However, during an active threat incident occupants must not congregate at these spots and instead simply get as far away as possible.
If the incident has occurred inside a facility and your occupants have exited the premises, they must be trained to stop others from entering the building in a way that is safe.
Hide
If it is unsafe to run away or escape from an active threat, then you must hide as soon as possible. Hiding must be done safely. To achieve this, we need to think about hiding in three separate parts:
Cover
When hiding, occupants must be placing a large enough physical object between themselves and the threat. The purpose of this object is to reduce the likelihood of physical harm they may experience from the active threat.
Objects which could be used as cover include:
- Doors
- Tables/Desks
- Large furniture (bookshelves, filing cabinets)
- Vehicles
Concealment
As important as it is to place yourself behind cover when hiding, equally important is concealment. This means you should not be visible when taking cover. For example, if an occupant takes cover behind a window, then yes, they are covered from physical harm however they are still visible and thus are not safe.
Barricade
Where possible it is best for an individual to barricade themselves to offer the best concealment and cover from the active threat. When doing this, it is imperative that the individual act quickly and quietly to not draw any attention to themselves.
When barricading yourself it is important to follow the below two steps:
- Secure
Of highest priority is to secure your barricade from intrusion. This means that any locks on windows or doors are locked & all resources must be used to barricade all entry points of the room. Your primary goal during this phase of barricading is ensuring if the threat comes close to you, it will be unable to harm you as it cannot enter your barricade.
- Behaviour
After securing the barricade there are additional steps that should be taken to ensure safety from the threat:
- Make sure that your lights are out: this ensures that people outside your barricade have less of a chance of knowing you are in there.
- Ensure you silence your mobile phone and turn off vibration as well. Many individuals think that simply silencing the phone is enough however vibrations can easily be heard in certain situations.
- Lay down on the floor & out of the way of any harmful materials that may enter the barricade.
Even once you have barricaded yourself you must continue to have a not permanent mentality about where you are situated. This means constantly re-assessing any alternative methods of escape, being vigilant for opportunities and mapping out an escape route based on your knowledge of the surroundings.
Tell
It is imperative the authorities are contacted on 000. The earlier this can be done, the better, as it gives authorities more time to respond to the threat in time.
When contacting the authorities, individuals should try to inform them:
- Situation: details of the exact active threat.
- Location: it is important to communicate exactly where the incident is occurring.
- Victims: who else is involved in the incident. Are there any victims which the authorities need to prepare for?
- Offenders: what type of person is creating the threat scenario? Do they have any weapons?
After informing the authorities they will be collecting information from a wide assortment of sources. However, the initial information that an individual can provide on first contact can prove invaluable to the authorities and be the difference in occupant safety.
Action
As an absolute last resort option, it may be required that an individual takes action to defend themselves from an active threat. The following should be kept in mind if such situation presents itself:
- Ensure this is the last resort. If there are any other opportunities for escape, hide & tell ensure those avenues have been explored first.
- Before taking any action, planning is critical for improving the odds for success.
- An individual is better off equipped with a weapon than without one when defending themselves. Improvise a weapon based on the resources in the immediate vicinity.
- If an individual is too aggressive when defending themselves, they can end up doing more harm than good to themselves. It is best to ensure that controlled aggression is employed during self-defence scenarios.
- Two heads are better than one. Wherever possible, it is best to employ teamwork to decrease the severity of the threat.
Responding to an active threat is extremely stressful and full of uncertainties. By following Escape, Hide & Tell, individuals are better equipped to handle these scenarios as safely as possible.
Contact us to learn how to best equip your occupants to respond to active threats as effectively as possible.